“Tea” App Breach Exposes 72,000 Women’s Selfies and IDs, In Shocking Irony, Safety App Becomes Security Nightmare
Table of Content
From #1 App to #DataBreach: The Rise and Fall of “Tea”
It skyrocketed to the top of the App Store.
It was the hottest new app for women sharing anonymous dating gossip.
And in less than a week, it became a cybersecurity disaster.
Tea, the women-only dating advice app that lets users post “red flags” and reviews about men they’ve dated, has suffered a major data breach — exposing over 72,000 images, including selfies and government-issued IDs used to verify users’ identities.
The irony?
An app built to make women feel safer in the dating world may have just put thousands of them at serious risk.
Viral Dating Review App for Women Hit by Data Leak, Including Verified IDs and Private Photos
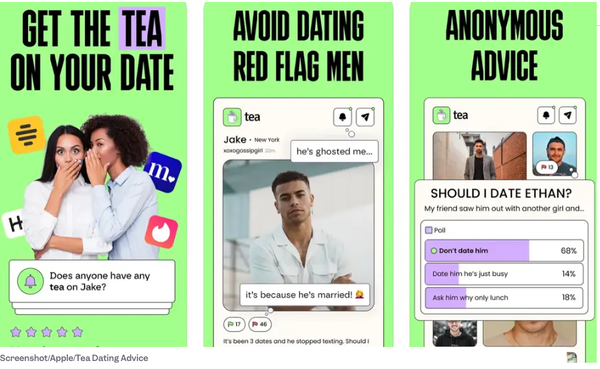
What Is the Tea App?
Tea launched as a private, invite-only community where women could:
- Post about men they’ve dated (with names, photos, locations)
- Flag behaviors like ghosting, lying, or emotional manipulation
- React with “green flags” or “red flags”
- Share DMs, screenshots (though the app blocks screenshots), and warnings
Think Yelp for dating, but exclusively for women, and completely anonymous.
It went viral almost overnight.
By Friday, July 25, Tea had over 2 million new user requests and was ranked #1 in the U.S. Apple App Store under “Social Networking.”
But its rapid success came with a dark underbelly.
The Breach: Legacy System, Massive Exposure
At 6:44 AM PST on July 25, Tea’s team detected unauthorized access to one of its systems.
In a statement to Business Insider, a company spokesperson confirmed:
“Preliminary findings indicate that the incident involved a legacy data storage system containing information from over two years ago.”
The breach exposed:
- 72,000 total images
- ~13,000 selfies and ID photos submitted during account verification
- 59,000 in-app images, including posts and direct messages
- User comments, usernames, and metadata
Crucially, the company says current user data was not affected, this was an old system that should’ve been decommissioned.
But here’s the problem: those 13,000 ID + selfie combos are a goldmine for identity thieves.
And the data didn’t stay hidden.
How It Got Worse: 4chan, Leaks, and Public Shaming
The breach was first reported by 404 Media, after hackers discovered the data publicly exposed on a server linked to Tea.
The files were dumped on 4chan’s infamous /b/ and /tech/ boards, where users quickly downloaded and shared them.
Why the backlash?
Because Tea had already sparked controversy.
Men’s rights groups and privacy advocates had criticized the app for allowing women to name, shame, and post photos of men without consent — sometimes based on hearsay.
Now, the tables turned.
Hackers on 4chan saw the breach as poetic justice:
“They wanted to expose men. Now they’re exposed.”
But the real victims?
The women who trusted the app with their most sensitive data.
The Real Danger: Identity Theft, Doxxing, and Blackmail
Having your dating review leaked is one thing.
But having your photo ID and selfie leaked together? That’s a different level of risk.
With both, bad actors can:
- Clone identities for fake accounts
- Apply for loans or credit cards
- Create deepfakes or revenge porn
- Dox or stalk users in real life
And because the IDs are linked to usernames and posts, anonymity, the app’s core promise, is completely shattered.
As one cybersecurity expert put it:
“This isn’t just a breach. It’s a target list for predators.”
Tea’s Response: Damage Control Mode
Tea has since:
- Launched a full investigation
- Hired third-party cybersecurity experts
- Shut down the exposed legacy system
- Posted a notice inside the app via “TaraTeaAdmin” (now with hundreds of angry comments)
- Published an Instagram story about growth, but no direct user alert
Critics say the response is too little, too late.
Many users are now demanding refunds (the app offers paid tiers), and some are calling for regulatory action.
Lessons Learned: Safety Apps Need Real Security
Tea’s story is a cautionary tale for the entire tech industry:
1. “Anonymous” Doesn’t Mean “Secure”
Just because users are anonymous doesn’t mean their real data isn’t stored. And if it is, it must be protected.
2. Legacy Systems Are Time Bombs
Old databases, forgotten servers, unpatched software, they’re low-hanging fruit for hackers. Decommission them before they leak.
3. Verification = Responsibility
If you ask users for IDs, you owe them enterprise-grade security. Storing them on an open Firebase bucket? Unforgivable.
4. Ethics and Privacy Go Both Ways
Yes, women deserve safe spaces to share dating trauma.
But platforms must balance empowerment with accountability, for all users.
What Should Users Do Now?
If you’re a Tea user:
- Delete your account immediately
- Change passwords for any linked accounts (email, social media)
- Monitor for phishing attempts or suspicious logins
- Consider a credit freeze if your ID was uploaded
- Report misuse to local authorities if your data is weaponized
And most importantly:
Never upload your ID to an app unless absolutely necessary, and always check its privacy policy.
The Bigger Picture: Can “Safety Apps” Ever Be Safe?
Tea isn’t alone.
Apps like Spotter, Peanut, and Hollaback also let users report harassment.
But none have faced a breach this severe.
As more social apps promise “safe spaces,” the question grows louder:
Who’s protecting the protectors?
Because without real security, transparency, and ethical design, even the most well-intentioned platforms can become digital danger zones.
Final Thought: Empowerment ≠ Exposure
Tea started with a powerful mission:
Give women a voice in a world where dating risks are real.
But by failing to protect that voice, it may have silenced trust for good.
In the digital age, true safety isn’t just about calling out red flags.
It’s about making sure your own data doesn’t become one.